Serious Internet Threat Explained, How It Can Affect You

The internet vulnerability Log4Shell, which affects millions of machines, is caused by Log4j, an obscure but practically ubiquitous piece of software. The software is used to track a variety of operations that occur behind the scenes in a variety of computer systems.
The most dangerous vulnerability she’s seen in her career, according to Jen Easterly, director of the US Cybersecurity & Infrastructure Security Agency. Hundreds of thousands, if not millions, of efforts, have already been made to exploit the flaw.
So, what exactly is this innocuous piece of the internet infrastructure, how can hackers take advantage of it, and what kind of havoc may it cause?
What Is the Purpose of Log4j?
Log4j keeps track of events, such as faults and ordinary system processes, and sends out diagnostic warnings to system administrators and users. The Apache Software Foundation provides open-source software.
When you enter in or click on a poor weblink and get a 404 error message, that’s an example of Log4j at work. There is no such webpage, according to the webserver that hosts the domain of the web link you attempted to access. It also uses Log4j to log the occurrence for the server’s system administrators.
Throughout software applications, similar diagnostic signals are employed. Log4j is used by the server in the online game Minecraft to log activity such as total memory utilized and user instructions sent into the console.
What Is Log4shell and How Does It Work?
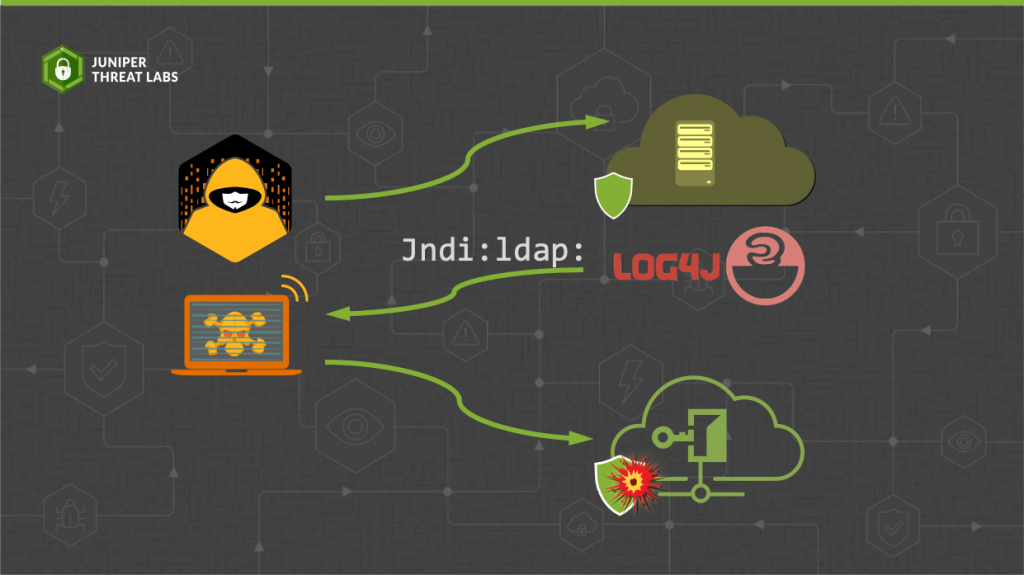
Log4Shell works by exploiting a Log4j feature that allows users to specify custom code for log message formatting.
If a separate server keeps a directory linking user names and actual names, this feature allows Log4j to log not just the username associated with each attempt to log in to the server, but also the person’s true name. The Log4j server must communicate with the server that stores the real names in order to accomplish this.
However, this type of code can be used for more than just log message formatting. Log4j allows third-party servers to send software code to the targeted computer that can execute a variety of tasks. This allows for illicit operations like stealing sensitive information, seizing control of the targeted system, and spreading malicious content to other users talking with the affected server.
Exploiting Log4Shell is rather straightforward. In just a few minutes, I was able to duplicate the issue in my copy of Ghidra, a reverse engineering framework for security researchers. Because the exploit has a low bar for use, it can be used by anyone with evil intent.
Log4j Is All Over the Place.
The place of Log4j in the software ecosystem is one of the primary issues concerning Log4Shell. Because logging is a standard part of most applications, Log4j is widely used. It’s used in a wide range of programs from software development tools to security products, in addition to popular games like Minecraft. It’s also used in cloud services like Apple iCloud and Amazon Web Services, as well as a wide range of applications from software development tools to security tools.
As a result, hackers have a wide range of targets to choose from, including ordinary people, service providers, source code developers, and even security experts. While large corporations like Amazon can quickly fix their web services to prevent hackers from abusing them, many more organizations will take longer to do so, and some may not even be aware that they need to.
The Amount of Harm That Can Be Done
Hackers are scouring the internet for unprotected servers and configuring devices to send malicious payloads. They query services (for example, web servers) and try to trigger a log message to carry out an attack (for example, a 404 error). The query contains maliciously designed text, which Log4j interprets as commands.
These instructions can either establish a reverse shell, allowing the attacker server to control the targeted server remotely, or they can make the target server a botnet. Botnets are groups of hijacked computers that work together to carry out coordinated attacks on behalf of the hackers.
Log4Shell is already being abused by a huge number of hackers. These range from ransomware gangs encrypting Minecraft servers to bitcoin mining hacking groups and hackers linked to China and North Korea attempting to obtain critical information from their geopolitical adversaries. The Belgian Ministry of Defense stated that Log4Shell was being used to attack its computers.
Despite the fact that the vulnerability was initially brought to the public’s attention on December 10, 2021, people are continuously finding new ways to exploit it.
Putting a Stop to the Bleeding
Because Log4j is frequently bundled with other applications, it’s difficult to tell if it’s being utilized in any specific software system. This necessitates system administrators inventorying their software to determine whether it is present. It’s considerably more difficult to eliminate the vulnerability if some people are unaware that they have a problem.
Because of Log4j’s many applications, there is no one-size-fits-all solution for patching it. Various ways will be required depending on how Log4j was integrated into a given system. It could necessitate a full system upgrade, as some Cisco routers have done, or updating to a new version of the software, as Minecraft has done, or manually eliminating the susceptible code for individuals who can’t update their program.
The software supply chain includes Log4Shell. Software, like physical goods, passes through various organizations and software packages before being packaged into a final product. Rather than going through a recall procedure when anything goes wrong, the software is usually “patched,” which means it is fixed in place.
Because Log4j is used in a variety of software products, spreading a patch involves collaboration from Log4j developers, software developers that utilize Log4j, software distributors, system operators, and users.
Typically, this causes a delay between when the remedy is released in the Log4j code and when people’s computers close the door on the vulnerability.
Time-to-repair estimates for software often range from weeks to months. However, if historical performance is any indication, the Log4j vulnerability will continue to be exploited for years to come.
You’re probably asking what you can do about it as a user. Unfortunately, determining whether a software package utilizes Log4j and whether it uses vulnerable versions of the software is difficult. You can help by following the advice of computer security experts and making sure all of your software is up to date.